SSH Tunnel
In computer networks, a tunnelling protocol allows a network user to access or provide a network service that the underlying network does not support or provide directly.
A Secure Shell (SSH) tunnel consists of an encrypted tunnel created through an SSH protocol connection. You can set up SSH tunnels to transfer unencrypted traffic over a network through an encrypted channel.
To set up a local SSH tunnel, configure an SSH client to forward a specified local port to a port on the remote machine. Once the SSH tunnel has been established, you can connect to the specified local port to access the network service. The local port does not have to be the same as the remote port.
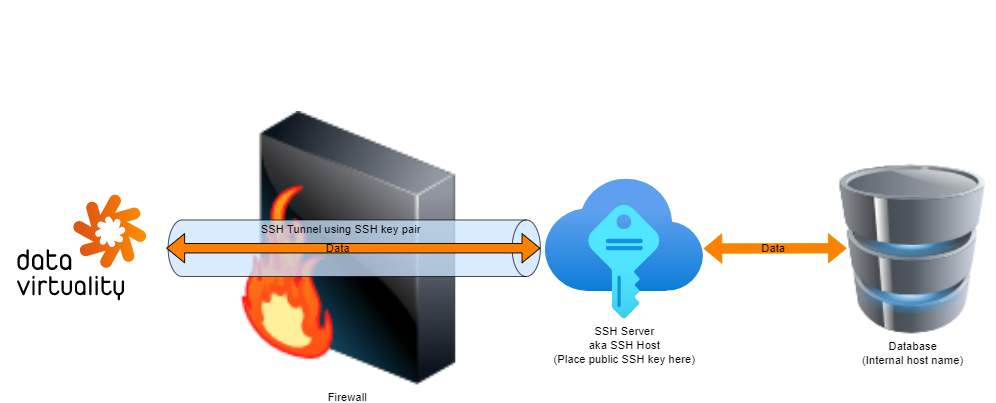
By default, Pipes has a pre-generated SSH key pair already created. Click on the ‘Key pair’ field to select one of the SSH keys from the drop-down list and follow the instructions for deploying the public key on your SSH host/server.
.png?inst-v=f98e813e-c010-4d00-927c-57c14d29038e)
If you need to generate additional keys, execute the following command in the code editor:
SELECT * FROM SYSADMIN_VDB.createSSHKeyPair ();;The new SSH keys should appear in the ‘Key pair’ drop-down list.
